Mobileforce
- General Resources
Table of Contents
ToggleIntroduction: Why CPQ Security Now Matters More Than Ever
The deal was worth $8.5 million—and it nearly fell apart because of a misconfigured CPQ rule that let an unauthorized user apply a steep discount without approval. By the time finance caught it, the quote had already been sent to the customer. This example is not uncommon. As CPQ platforms become deeply embedded in enterprise revenue operations, they’re no longer just sales tools—they’re high-value targets. These systems host pricing logic, discount thresholds, contract terms, and margin controls. For IT and security leaders, that makes CPQ more than just mission-critical—it makes it a potential liability.
The stakes have never been higher. Consider the consequences of CPQ security failures:
- Financial Impact: Unauthorized discounting or pricing manipulation can cost companies millions in lost margins.
- Competitive Exposure: Leaked pricing strategies or special terms can undermine your market position.
- Regulatory Penalties: In regulated industries, mistakes or security breaches can trigger severe compliance penalties.
- Reputational Damage: Customer trust erodes quickly when sensitive quote information is compromised.

A recent Forrester study found that 73% of enterprises experienced at least one security incident related to their sales technology stack in the past 24 months. With the average cost of a data breach now exceeding \$4.45 million (according to IBM’s Cost of a Data Breach Report), the business case for securing CPQ platforms has become overwhelming.
Enterprise CPQ deployments are typically integrated with CRMs (like Salesforce or HubSpot), ERPs (like NetSuite or SAP), contract management systems, and even billing and invoicing engines. This interconnected architecture creates a broader attack surface that, if not properly secured, can lead to unauthorized access, compliance failures, or worse—financial data breaches.
The traditional approach to CPQ security—implementing basic authentication and limited access controls—is no longer sufficient. Modern enterprise environments demand a comprehensive security model that addresses:
- Identity assurance: Verifying that users are who they claim to be
- Contextual access: Ensuring appropriate permissions based on role, location, and device
- Cross-system security: Maintaining protection across integration points
- Continuous monitoring: Detecting and responding to suspicious activities
- Compliance documentation: Providing evidence for regulatory requirements
Mobileforce CPQ stands apart as a cloud-native solution purpose-built with enterprise-grade security in mind. While legacy CPQ tools often treat security as an afterthought or a bolt-on feature, Mobileforce embeds identity, access, and compliance controls at the arOASISchitectural level—ensuring security and scalability go hand in hand.

Implementing SSO in CPQ Platforms
Single Sign-On (SSO) is the cornerstone of enterprise-grade authentication. It allows users to log in to multiple systems using one set of secure credentials, simplifying access while tightening security. For CPQ systems, which are used by sales, operations, finance, and external partners, SSO is essential.
Why SSO Matters in CPQ:
- Eliminates Password Fatigue and Security Risks: By providing a single set of secure credentials across systems, SSO dramatically reduces the likelihood of password reuse, weak passwords, or credentials being written down, significantly enhancing your security posture across the entire sales technology stack.
- Delivers Seamless Enterprise User Experience: Sales teams can move effortlessly between CRM, CPQ, and other systems without interruption, using their existing corporate identity provider (IdP) credentials, eliminating productivity barriers and reducing authentication-related support tickets by up to 50%.
- Centralizes Critical Security Governance: All authentication policies—including multi-factor authentication (MFA) requirements, password complexity rules, login attempt limitations, and conditional access based on location or device—can be managed from a single control plane, ensuring consistent enforcement across your entire business application ecosystem.
Key Industry Standards:
- SAML 2.0: XML-based federated identity protocol widely adopted by large enterprises.
- OpenID Connect (OIDC): An identity layer on top of OAuth2, more modern and REST-friendly.
The Mobileforce Advantage:
Mobileforce CPQ natively supports both SAML 2.0 and OIDC, allowing fast, secure, and scalable SSO deployment across desktop and mobile. Unlike some CPQ vendors that require development-heavy custom setups, Mobileforce offers prebuilt integrations with IdPs like Okta, Azure AD, and Google Workspace out of the box. This minimizes time-to-deploy and ensures compliance with enterprise authentication standards from day one.
Administrators can map user roles automatically based on identity attributes like department, group membership, or geographic region—allowing fine-grained access provisioning the moment a user logs in.
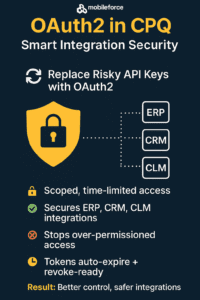
OAuth2 in CPQ: Secure, Tokenized Access for APIs and Services
Modern enterprises rely on rich integrations between systems—and CPQ is no exception. From pricing updates pulled from ERP to contract generation via DocuSign, a CPQ platform must orchestrate workflows across multiple tools. This makes OAuth2 a critical part of the CPQ security framework.
The complexity of today’s enterprise sales tech stack is staggering. A typical CPQ implementation might integrate with 5-10 other systems, each requiring secure data exchange:
- ERP systems for product and pricing master data
- CRM platforms for customer and opportunity information
- Contract management systems for legal terms and approvals
- E-signature solutions for deal closure
- Business intelligence tools for quote analytics
- PLM systems for product specifications
- Customer portals for self-service quoting
Without a robust security framework like OAuth2, each integration becomes a potential vulnerability. Traditional integration methods often rely on shared credentials or API keys that, if compromised, grant broad access across systems.
What is OAuth2 in a CPQ Context?
OAuth2 is a secure authorization protocol that allows applications to access data on behalf of users without exposing their passwords. It uses access tokens to grant and restrict access to specific resources for a defined period.
Let’s illustrate with a common scenario: A sales rep creating a quote that needs to pull customer-specific pricing from SAP. Without OAuth2, the CPQ might use a service account with permanent, broad access to SAP data. With OAuth2, the CPQ requests a short-lived token with permissions limited to just the pricing data needed for that specific customer—dramatically reducing the potential attack surface.
In CPQ, OAuth2 secures:
- APIs for real-time product configuration
- Price retrieval from external sources
- Order submission workflows into ERP
- CRM data access for opportunity syncing
- Partner portal access for channel quoting
- Analytics connections for quote performance data
- Approval workflows across departmental boundaries
Key Security Benefits of OAuth2:
Enterprise-Grade Scoped Access Control: Define precisely what data and functionality each integration partner or application can access within your CPQ ecosystem, creating security boundaries that prevent lateral movement in case of a breach—for example, allowing a partner portal to access only specific product catalogs while keeping pricing strategies and approval workflows completely isolated.
Dynamic Token Management with Rapid Response Capability: Implement short-lived access tokens with automatic expiry and rotation mechanisms that dramatically reduce the vulnerability window compared to traditional API keys, enabling security teams to revoke access within minutes if suspicious activity is detected without disrupting other system integrations.
Secure Third-Party Ecosystem Enablement: Safely extend your CPQ capabilities through external tools and applications (such as analytics platforms, contract management systems, or custom sales tools) while maintaining granular control over their access patterns, ensuring these integrations enhance rather than compromise your security posture.
The Mobileforce Advantage:
Mobileforce’s API architecture is built around OAuth2. It offers:
- Microservice-Specific Security Boundaries: While conventional CPQ platforms use monolithic API security with broad access grants, Mobileforce implements a sophisticated microservice architecture with dedicated, scope-limited access tokens for each functional domain (Quoting API, Pricing API, Approval API, Catalog API)—creating security isolation that prevents credential compromise in one area from affecting other system components.
- Complete Token Lifecycle Governance Platform: Mobileforce provides comprehensive token management capabilities including automated refresh mechanisms, configurable expiration policies, and emergency revocation capabilities that enable security teams to respond to potential compromises within seconds—dramatically reducing the risk window compared to traditional API key approaches used by legacy CPQ systems.
- Self-Service Integration Security Management: Unlike competitors requiring developer expertise for API security configuration, Mobileforce offers an intuitive administrative interface with automated client registration, interactive token diagnostics, and visual permission assignment—enabling operations teams to securely connect external systems without security compromises or development bottlenecks.
This enables Mobileforce to connect securely with external systems while ensuring zero-trust API access—a vital requirement for enterprise IT teams managing sprawling digital ecosystems.
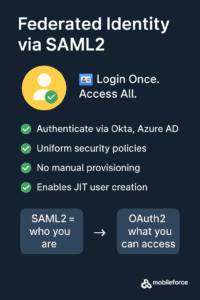
Federated Authentication via SAML2: Enterprise Standard Made Easy
As organizations embrace hybrid work and global expansion, managing user access across multiple systems becomes increasingly complex. That’s where federated authentication using SAML2 comes in—it allows users to log into third-party platforms like a CPQ system using their existing corporate credentials, governed by the enterprise Identity Provider (IdP).
Why SAML2 is Critical for Enterprise CPQ
Unified Enterprise Security Control Plane: Authentication policies, session management, and identity governance are administered centrally through sophisticated platforms like Okta or Azure AD, eliminating security inconsistencies across applications and providing a complete view of user access patterns across your entire technology ecosystem.
Frictionless Multi-System User Experience: Sales teams, channel partners, pricing analysts, and approval stakeholders can navigate seamlessly between your CRM, CPQ, ERP, and contract systems without encountering login barriers or maintaining separate credentials, dramatically reducing authentication friction that typically slows sales processes and creates security shortcuts.
Consistent Security Policy Enforcement: Critical security controls such as adaptive multi-factor authentication, device compliance verification, network location restrictions, and suspicious login detection are uniformly applied across all integrated systems, closing security gaps that often exist between standalone applications.
SAML2 vs. OAuth2
SAML2 handles authentication—verifying who the user is.
OAuth2 handles authorization—what the user or system can access.
Both are critical for CPQ systems that need to tightly control access across roles, devices, and APIs.
The Mobileforce Advantage:
Mobileforce streamlines federated authentication via:
- Enterprise-Class Identity Provider Integration: While other CPQ platforms require complex integration work or offer limited IdP support, Mobileforce provides production-ready, fully tested connections with all major identity providers (Okta, Azure AD, Ping Identity, ForgeRock, OneLogin)—complete with advanced features like step-up authentication for sensitive operations and certificate auto-rotation that eliminate common security gaps in federated implementations.
- Zero-Code Security Configuration Experience: Unlike competitors that require developer resources or professional services engagement to configure security features, Mobileforce offers an intuitive administrative interface for identity and access management that enables non-technical teams to implement enterprise-grade security without writing a single line of code or editing configuration files—reducing implementation time from weeks to hours.
- Intelligent Just-in-Time Provisioning Engine: Mobileforce’s sophisticated JIT provisioning system automatically creates fully-configured user accounts upon first login based on multiple SAML assertion attributes (department, geography, role, product line)—not only eliminating manual user provisioning but also ensuring that role assignments and permissions precisely match your organizational structure without ongoing administration.
By using these features, enterprises can roll out secure CPQ access globally—without provisioning every user manually or risking inconsistent access policies.
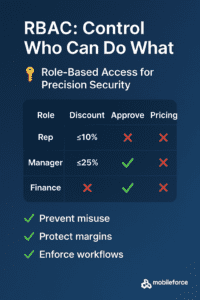
Role-Based Access Control (RBAC): Precision Control Built In
One of the most overlooked security vectors in CPQ platforms is internal misuse or over-permissioned users. In sales operations, it’s not uncommon for reps to experiment with pricing, create unauthorized bundles, or bypass approval processes—all of which can erode margin or create risk. This makes Role-Based Access Control (RBAC) absolutely essential.
The financial impact of inadequate access controls in CPQ systems can be substantial. Consider these real-world scenarios we’ve observed:
- A global manufacturer discovered that sales reps were offering unauthorized discounts of up to 30% on high-margin products, resulting in \$2.3M in lost profit over a single quarter.
- A SaaS company found that customer success managers had been modifying pricing tiers in their CPQ system, creating inconsistent renewal quotes and triggering costly revenue recognition issues.
- A distribution company identified that regional managers were creating custom product bundles without engineering approval, leading to fulfillment problems and customer satisfaction issues.
These cases aren’t about malicious behavior—they’re about well-intentioned employees working around processes because they lack appropriate guardrails. Proper RBAC implementation prevents these scenarios by ensuring users have exactly the permissions they need—no more, no less.
What Is RBAC in CPQ?
RBAC defines what actions a user can take in a system based on their role. In a CPQ platform for example, roles can typically map to:
- Sales Rep – create quotes, apply standard discounts
- Sales Manager – approve quotes with flexible pricing
- Pricing Analyst – manage price books, discounting rules
- Finance or Legal – access contract terms or flag policy violations
- Channel Partner – limited product catalog and pricing visibility
- Executive – view-only access to all quotes and analytics
- System Administrator – configure workflows and integration settings
- Product Manager – manage product configurations and rules
Permissions can be tied to actions such aslike:
- Creating or modifying quotes
- Applying discount tiers
- Editing products or bundles
- Changing approval rules
Why Fine-Grained Permissions Matter
Prevents Costly Unauthorized Modifications: Sophisticated permission controls eliminate the risk of unauthorized pricing changes, discount manipulation, or product configuration alterations that could potentially cost organizations millions in lost margins—one enterprise customer discovered unauthorized discounting was eroding margins by 4.3% before implementing proper permission controls.
Enables Regulatory Compliance Through Structural Controls: By enforcing separation of duties, approval hierarchies, and change documentation, robust RBAC directly supports compliance with SOX, ISO 27001, GDPR, and industry-specific regulations like HIPAA or DFARS, preventing costly violations and simplifying audit processes that typically consume substantial IT and finance resources.
Creates Comprehensive Digital Accountability: Advanced permission systems create crystal-clear visibility into quote lifecycle activities—identifying precisely who modified what, when, and under what authority—transforming security audits from multi-week investigations into on-demand reports and providing early warning of potential process violations before they impact financial results.
The Mobileforce Advantage:
Mobileforce takes RBAC to a whole new level with:
- Advanced Hierarchical Role Architecture: Unlike basic CPQ systems that offer flat permission structures, Mobileforce allows you to construct sophisticated nested permission hierarchies that precisely mirror your real-world management chains and approval flows (regional directors → territory managers → account executives → sales associates), ensuring that authority boundaries in your organization are perfectly reflected in system capabilities.
- Context-Sensitive Dynamic Permission Controls: Mobileforce uniquely enables permission variations based on multiple business factors simultaneously—such as deal size, geography, product line, customer segment, or quote stage—allowing nuanced rules like enabling a sales rep to apply a 15% discount on domestic SMB deals under \$50,000, while requiring tiered approvals for enterprise or international opportunities.
- Intuitive Visual Permission Designer: While most CPQ platforms require complex coding or script-based permission configuration, Mobileforce offers an industry-leading drag-and-drop visual interface for role definition and testing that empowers business administrators to create, simulate, and validate complex permission models without developer intervention—reducing security configuration time by up to 80% compared to conventional CPQ solutions.
Moreover, Mobileforce supports custom permission sets, allowing administrators to create hybrid roles for users who wear multiple hats (e.g., a RevOps user with access to quote templates and analytics dashboards, but not approval rights).

Compliance, Monitoring, and Audit Logging
Security isn’t just about access—it’s also about accountability. In regulated industries, companies are required to prove that only the right users accessed sensitive data, that approval workflows were followed, and that no unauthorized changes were made to customer quotes or pricing logic. Enter compliance controls and audit logging.
What Compliance Means in the CPQ Context
CPQ systems often intersect with regulations such as:
- SOX (Sarbanes-Oxley) – Traceability of pricing approvals and discount authorizations.
- GDPR – Controlled access to and usage of personal data in customer quotes.
- ISO 27001 – Enforcement of access controls, logging, and risk mitigation strategies.
As sales operations scale globally, these frameworks become non-negotiable for IT and compliance leaders.
The Role of Monitoring and Logging
Enterprise-Grade Immutable Audit Trails: Implement tamper-proof, comprehensive logging that captures every detail of quote modifications, approval actions, pricing overrides, and user authentication events—creating an unalterable record that satisfies the most stringent regulatory requirements while providing forensic-level detail for security investigations or compliance audits.
High-Precision Chronological Event Tracking: Utilize cryptographically secured timestamps for all system events to establish definitive sequencing of activities across users and systems, ensuring that approval processes, pricing changes, and configuration modifications can be precisely reconstructed for post-incident reviews or to resolve customer disputes about quote terms and conditions.
Proactive Security Intelligence: Deploy sophisticated real-time monitoring capabilities that can identify unusual patterns, potential policy violations, or suspicious activities—such as off-hours quote modifications, unusual discount patterns, or repeated approval rejections—and alert administrators before these anomalies develop into significant security incidents or financial losses.
Enterprise Security Ecosystem Integration: Implement comprehensive data retention policies and standardized export capabilities that allow CPQ security events to be incorporated into enterprise SIEM systems, enabling correlation with other security telemetry and providing security operations centers with visibility into sales technology activities alongside other critical systems.
The Mobileforce Advantage:
Mobileforce comes audit-ready out of the box. Key features include:
- Comprehensive Audit Infrastructure: While competitors offer basic logging, Mobileforce provides an enterprise-caliber audit system that records every aspect of system activity—including quote changes, approval actions, role modifications, and data exports—with detailed user attribution, IP address tracking, and cryptographic timestamps that satisfy the most demanding compliance requirements.
- Industry-Leading Real-Time Security Intelligence: Mobileforce’s exclusive Event Intelligence Platform provides security administrators with customizable real-time activity dashboards and sophisticated filtering capabilities that enable instant identification of potential security anomalies or compliance violations across users, territories, or product lines—delivering security insights that typical CPQ platforms cannot provide without custom development.
- Enterprise SIEM Ecosystem Integration: Unlike CPQ platforms with closed or proprietary logging formats, Mobileforce offers native integration with leading security information and event management systems including Splunk, Azure Sentinel, and ELK Stack—allowing your security operations team to incorporate CPQ activity into their comprehensive threat monitoring without complex data transformation or connector development.
- Compliance Intelligence Visualization: Mobileforce’s proprietary compliance dashboards transform raw audit data into actionable business intelligence, providing at-a-glance visibility into critical controls such as discount threshold adherence, approval workflow compliance, and exception frequency—enabling proactive governance rather than reactive investigations.
These features make Mobileforce not just secure—but transparent and accountable.

Summary: What Makes a CPQ Platform Truly Enterprise-Ready
To truly qualify as “enterprise-ready,” a CPQ platform must go far beyond configurability and quote speed. It must become a trusted, secure node in the organization’s revenue infrastructure.
Here’s how the top CPQ platforms stack up—and where Mobileforce leads:
Enterprise Feature | Industry Standard | The Mobileforce Advantage |
SSO via SAML2 or OIDC | Basic support for 1-2 major IdPs | Comprehensive IdP ecosystem with advanced features like certificate auto-rotation, step-up authentication, and attribute-based provisioning |
OAuth2-secured APIs | General token-based security | Microservice-specific security boundaries with customizable scopes, full lifecycle governance, and integrated monitoring |
Role-based access (RBAC) | Static role assignments with limited contexts | Dynamic, multi-factor permission system with visual designer that enables role creation without coding or scripts |
Federated Identity Management | Manual account creation with basic attribute mapping | Intelligent JIT provisioning with complex rule support based on multiple assertion attributes |
Compliance & Audit Logs | Basic event logging with limited retention | Cryptographically secured audit trail with real-time analytics dashboard and native SIEM integration |
Admin Self-Service Configuration | Typically requires developer support | Complete administrative interface for all security functions without technical expertise |
Support for Least Privilege Model | Coarse-grained permissions | Ultra-granular permission segmentation by geography, product line, deal attributes, and workflow stage |
Security Ecosystem Integration | Limited or proprietary interfaces | Open architecture with certified integrations to enterprise security systems |
Mobileforce’s security features aren’t bolted on—they’re architected fromarchitected in from the foundation, creating a fundamental difference in both capability and reliability compared to platforms where security was an afterthought.

Final Thoughts
Securing your CPQ platform is no longer an afterthought—it’s a strategic imperative. As enterprise quoting becomes more automated, integrated, and intelligent, the risk of misuse, unauthorized access, and compliance violations increases dramatically. Achieving true CPQ security requires cross-functional alignment: IT security teams must ensure the platform meets enterprise standards and integrates with monitoring infrastructure; sales operations leaders need to define access roles that balance control with productivity; compliance officers must verify support for regulatory frameworks; and finance leaders should confirm controls that protect pricing integrity and margins.
A phased approach works best—start by assessing your current CPQ security posture, then design an architecture aligned with your enterprise identity strategy. Implement core controls like SSO, RBAC, and audit logging, integrate with systems like SIEM, and establish real-time monitoring. Finally, optimize based on usage patterns. By choosing a CPQ platform that supports modern authentication, enforces granular access, and simplifies compliance, you’re not just securing workflows—you’re enabling safe, scalable growth.
Mobileforce CPQ delivers all of this and more, with unmatched flexibility, ease of configuration, and built-in integrations to make security a seamless part of your quoting process. Our security-first architecture has been validated by third-party security assessments and is trusted by companies in highly regulated industries including finance, healthcare, and defense contracting.
Looking for a secure CPQ platform that your IT and compliance teams will love as much as your sales teams do? Request a demo with Mobileforce and see enterprise-ready security in action. Our security specialists can provide a comprehensive assessment of your current CPQ security posture and demonstrate how Mobileforce can elevate your enterprise security capabilities.
Frequently Asked Questions
What makes a CPQ platform “enterprise-ready” from a security perspective?
An enterprise-ready CPQ platform must support industry-standard authentication protocols (SSO, SAML2, OAuth2), implement granular role-based access controls, provide comprehensive audit trails, enable compliance with relevant regulations, and integrate with existing enterprise security infrastructure. These capabilities ensure that sensitive pricing, product, and customer data remain protected while enabling appropriate access for users across the organization.
How does Single Sign-On (SSO) improve CPQ security?
SSO significantly enhances CPQ security by eliminating the need for multiple passwords, centralizing authentication policies, enabling consistent enforcement of multi-factor authentication, reducing credential sharing, and providing a single point to revoke access when employees leave the organization. By integrating with corporate identity providers like Okta or Azure AD, SSO ensures that CPQ access follows the same strict policies as other enterprise systems.
What’s the difference between SAML2 and OAuth2 in CPQ platforms?
While both are critical for secure CPQ implementations, SAML2 and OAuth2 serve different purposes. SAML2 handles authentication (proving who users are) and enables federated identity across systems, while OAuth2 manages authorization (what users can access) through secure, scoped tokens. Enterprise CPQ platforms need both: SAML2 for secure user logins and OAuth2 for secure system-to-system integrations with CRMs, ERPs, and other business tools.
Why is Role-Based Access Control (RBAC) essential for CPQ security?
RBAC prevents unauthorized pricing changes, accidental configuration modifications, and approval workflow bypasses by ensuring users can only access functionality appropriate to their role. This precision control preserves pricing integrity, maintains consistent discounting practices, enforces approval hierarchies, and creates clear audit trails—all critical for preventing margin erosion and maintaining compliance. Without proper RBAC, even well-intentioned users can cause significant financial damage through unauthorized discounting or configuration changes.
How does a secure CPQ platform help with regulatory compliance?
A secure CPQ platform supports regulatory compliance through several mechanisms: immutable audit logs capture all quote and pricing changes for SOX compliance; role-based permissions enforce separation of duties; data protection features safeguard personal information in accordance with GDPR and CCPA; and comprehensive reporting capabilities provide evidence for auditors. Additionally, enterprise CPQ platforms can enforce compliant workflows for regulated industries like healthcare, financial services, and government contracting.
Can cloud-based CPQ platforms be as secure as on-premises solutions?
Modern cloud-based CPQ platforms typically offer superior security compared to on-premises solutions. Cloud platforms benefit from continuous security updates, dedicated security teams, regular penetration testing, and compliance certifications that would be cost-prohibitive for individual companies to maintain. With features like end-to-end encryption, cloud security posture management, and integration with enterprise identity providers, cloud-based CPQ platforms like Mobileforce provide enterprise-grade security while eliminating the maintenance burden of on-premises systems.
How should organizations evaluate CPQ security during the vendor selection process?
When evaluating CPQ platform security, organizations should: request SOC 2 or ISO 27001 compliance documentation; verify support for your identity provider and authentication protocols; assess granularity of permission controls; examine audit logging capabilities; review API security features; check compliance with industry-specific regulations; and understand data protection measures. Additionally, include your security team in vendor demonstrations to ensure the CPQ platform meets enterprise security standards before implementation begins.
What are the risks of using a CPQ platform with inadequate security controls?
Inadequate CPQ security can lead to multiple serious consequences: unauthorized discounting that erodes profit margins; exposed pricing strategies that competitors can exploit; compliance violations resulting in regulatory penalties; data breaches containing sensitive customer information; inconsistent quote approvals bypassing financial controls; and inability to trace the source of pricing errors or fraud. These risks make CPQ security a critical consideration for finance, IT, and sales leadership alike.